Five new zero-day vulnerabilities have been discovered this year in Ivanti Secure VPN, a popular VPN solution used by organizations worldwide. The two Ivanti Secure VPN zero-day vulnerabilities reported on Jan. 10, 2024 are covered extensively below.
We have updated this article to reflect the three new Ivanti zero-day vulnerabilities that have been reported since then, as well as two Ivanti vulnerabilities from 2021 that appear to have resurfaced. While the latest zero-day vulnerabilities allow an unauthenticated attacker to execute remote code and compromise systems, the two vulnerabilities from 2021 allow the attacker to elevate its privileges inside the compromised network.
Ivanti released new patches on Feb. 8, 2024 for some of these vulnerabilities; those specifics are detailed at the end of this article.
Ivanti Secure VPN vulnerabilities reported on Jan. 10, 2024: CVE-2023-46805 and CVE-2024-21887
On Jan. 10, 2024, Ivanti published an official security advisory and knowledge base article about two zero-day vulnerabilities, CVE-2023-46805 and CVE-2024-21887, affecting all supported versions of Ivanti Connect Secure (previously known as Pulse Connect Secure) and Ivanti Policy Secure Gateways.
- CVE-2023-46805 is an authentication bypass vulnerability in the web component of Ivanti Connect Secure and Ivanti Policy Secure. It allows an attacker to access restricted resources by bypassing control checks.
- CVE-2024-21887 is a command injection in web components of Ivanti Connect Secure and Ivanti Policy Secure. It allows an authenticated administrator to send specially crafted requests and execute arbitrary commands on the appliance, and can be exploited via the internet.
When combined, these two zero-day vulnerabilities allow an attacker to run commands on affected appliances.
Patrice Auffret, founder, chief executive officer and chief technology officer at ONYPHE, a French cyber defense search engine dedicated to attack surface discovery and attack surface management, told TechRepublic in an email interview on Jan. 12, 2024 that 29,664 Ivanti Secure VPN appliances are connected to the internet, with more than 40% of the exposed systems being in the U.S., followed by Japan (14.3%) and Germany (8.48%) (Figure A).
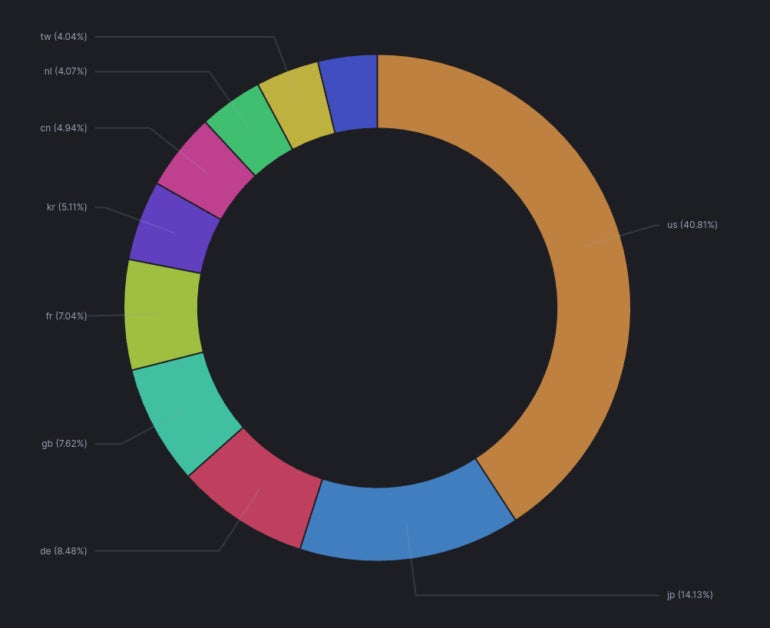
Exploitation of these zero-day vulnerabilities in the wild
U.S.-based cybersecurity company Volexity discovered both vulnerabilities during an incident response investigation across multiple systems. The incident response revealed that a threat actor modified several files placed on the Ivanti Connect Secure VPN appliance (Figure B).
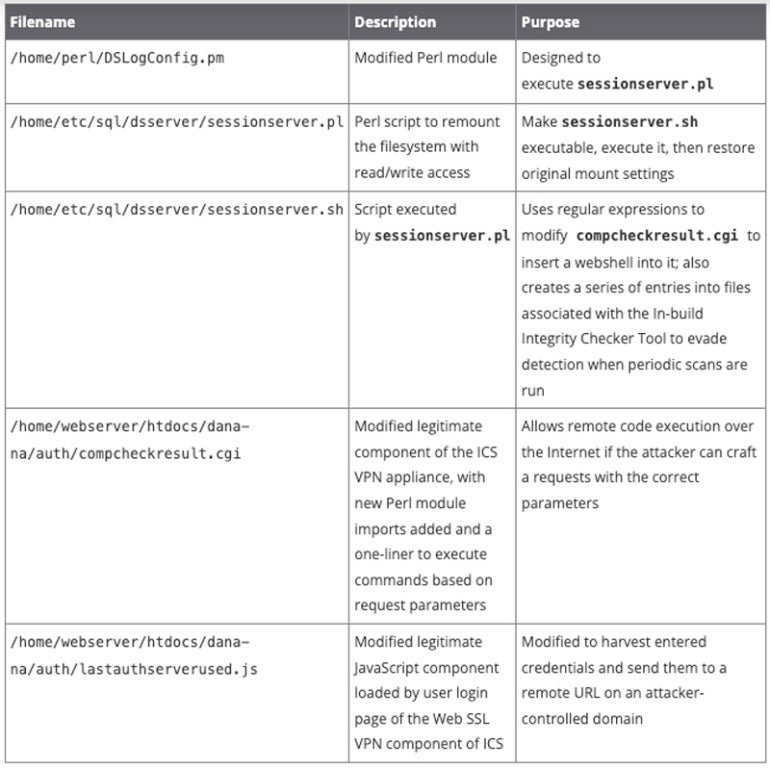
Volexity also believes a number of files have been created and used/executed in the system’s temporary folder (/tmp) but were no longer available for investigation at the time of the incident response, such as:
- /tmp/rev
- /tmp/s.py
- /tmp/s.jar
- /tmp/b
- /tmp/kill
A Python-based proxy utility, PySoxy, believed to be s.py, was found on a disk image. It is a SOCKS5 proxy script freely available on the internet.
The threat actor, dubbed UTA0178 by Volexity, deployed webshells and modified files to allow credential theft before moving from system to system using the compromised credentials. The threat actor kept collecting newly harvested credentials on every system they hit and was observed dumping a full image of the Active Directory database. Finally, the attacker modified the JavaScript loaded by the web login page for the VPN appliance to capture any credentials provided to it. The legitimate lastauthserverused.js script was modified to send the stolen credentials to an attacker-controlled domain: symantke(.)com.
Once in possession of credentials, the threat actor explored the network, looking at user files and configuration files, and deployed more webshells on the network, including a custom webshell dubbed GLASSTOKEN.
Custom GLASSTOKEN webshell
While the threat actor made use of several public and known tools, GLASSTOKEN was deployed in two slightly different versions.
The first version includes two code paths, depending on the parameters provided in the request. The first path is used to relay a connection, while the second one is used to execute code that is decoded from hexadecimal before being base64 decoded. According to Volexity’s observations, the threat actor used it mostly to execute PowerShell commands.
The second version of the webshell is close to the first one except that it misses the proxying feature, only allowing code execution.
Full code for those webshells has been provided by Volexity.
Ivanti Secure VPN vulnerabilities reported after Jan. 10, 2024: CVE-2024-21888, CVE-2024-21893, CVE-2024-22024
On Jan. 22, 2024, a new Ivanti security advisory was released: “As part of our ongoing investigation into the vulnerabilities reported on 10 January in Ivanti Connect Secure, Ivanti Policy Secure and ZTA gateways, we have discovered new vulnerabilities. These vulnerabilities impact all supported versions – Version 9.x and 22.x.”
The two new vulnerabilities, CVE-2024-21888 and CVE-2024-21893, allow an attacker to bypass authentication and access restricted resources on vulnerable devices and to elevate its privileges to those of an administrator. As reported by Mandiant, “Successful exploitation would bypass the initial mitigation provided by Ivanti on Jan. 10, 2024.”
On Feb. 8, 2024, another new vulnerability was reported by Ivanti; CVE-2024-22024 allows an attacker to access certain restricted resources without authentication. Ivanti maintains a knowledge base with all updates and reports that “the situation is still evolving.”
Exploitation of two older Ivanti Secure VPN vulnerabilities: CVE-2021-42278 and CVE-2021-42287
On Feb. 5, 2024, NCC Group, a global cybersecurity and software resilience company, reported what they believe to be exploitation of older vulnerabilities affecting Ivanti Secure Connect VPN as a means of privilege escalation, following the successful compromise of an Ivanti Secure Connect VPN instance using the vulnerabilities reported by Volexity. NCC Group researchers write that CVE-2021-42278 and CVE-2021-42287 are “vulnerabilities in Active Directory that when combined can allow a regular user to impersonate a domain administrator.”
David Brown, managing consultant, Digital Forensics and Incident Response at NCC Group, said in a statement provided to TechRepublic that, “Since the vulnerabilities were discovered, we’ve been assisting numerous clients, helping them understand whether they may have been compromised. In this process we’ve identified what we believe are cases of threat actors attempting to combine the vulnerabilities to gain access to a network. Our advice to anyone using Ivanti VPN is to follow patching guidance from the manufacturer and to carry out a thorough investigation, to hunting for indicators of compromise. Acting now is key.”
How to detect these Ivanti VPN security threats
Network traffic analysis
Careful analysis of the outbound traffic from the VPN appliance can detect suspicious activity. Aside from the legitimate connection back to pulsesecure.net and any other customer-related configured integration (SSO, MFA etc.), any suspicious activity should be analyzed. Examples as observed by Volexity are curl requests to remote websites, SSH connections to remote IP addresses, or encrypted communications to hosts that are not associated with providers or device updates.
Activity on the inbound network traffic from IP addresses associated with the VPN appliance should also be checked carefully. Suspicious traffic that might be observed on such connections can be RDP or SMB activity to internal systems, SSH connection attempts or port scanning, to name a few.
VPN device log analysis
Any indication that the VPN appliances log files have been wiped or disabled is a strong indicator of compromise, in case it was previously active.
Requests for files in atypical paths in the logs should also be concerning and analyzed, as threat actors might store or manipulate files out of the usual folders.
Integrity Checker tool
The In-Build Integrity Check tool can be used to run automatically and detect new or mismatched files. As written by Volexity’s researchers, “if any new or mismatched files are listed, the device should be considered compromised.”
Ivanti provides an external version of the Integrity Checker tool, which should be used in case the system is suspected of being compromised. The tool should only be installed and launched after all forensic evidence has been collected from the system — in particular a memory image because the execution of the tool will reboot the appliance and possibly overwrite evidence data.
Patches for some Ivanti VPN vulnerabilities
Organizations need to patch all domain controllers against CVE-2021-42278 and CVE-2021-42287 and set the machine account quota for standard users to zero.
On Feb. 8, 2024, Ivanti released new patches that replace patches made available on Jan. 31 and Feb. 1, 2024. Ivanti highly recommends users upgrade to the latest version of Ivanti Connect Secure or Ivanti Policy Secure to ensure the latest security and stability fixes are deployed.
Ivanti also recommends users migrate to Ivanti Neurons for ZTA to benefit from the newest architecture of these products.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


