
CVE-2022-30190, also known as “Follina”, is a remote code execution (RCE) vulnerability that affects Microsoft Office, reported on May 27, 2022.
How can Follina vulnerability be exploited by attackers?
The way it goes is as follows:
- A Microsoft Office .DOC file crafted by an attacker is sent to a target.
- The .DOC file references a HTTPS: link leading to an HTML file containing obfuscated JavaScript code.
- The JavaScript code references another link with an identifier MS-MSDT: instead of the usual HTTPS: identifier.
- Windows operating systems open the Microsoft Support Diagnostic Tool (MSDT) and run code contained in the provided link.
- Depending on the code executed on the targeted system, the attacker might facilitate further compromise or take control of the affected system.
The Follina vulnerability can therefore easily be triggered by sending phishing emails to targets, either containing the malicious .DOC file or a link leading to it.
How dangerous is Follina?
Nikolas Cemerikic, cybersecurity engineer, Immersive Labs, says:
“What makes Follina stand out is that this exploit does not take advantage of Office Macros and, therefore, it works even in environments where Macros have been disabled entirely. All that’s required for the exploit to take effect is for a user to open and view the Word document, or to view a preview of the document using the Windows Explorer Preview Pane. Since the latter does not require Word to launch fully, this effectively becomes a 0-click attack.”
Cemerikic adds that “this vulnerability is not specifically synonymous with Microsoft Word or Outlook. Although the only recorded cases so far of this vulnerability being exploited in the wild have been leveraged through the use of Microsoft Word and Outlook, in theory, any office product which handles oleObject relationships is vulnerable. As oleObject relationships are not specific to Word, it is likely that in the future we may see this vulnerability being exploited in other Office applications as well.”
Also, according to Huntress, it is possible to trigger the vulnerability without opening the file, by crafting a specific .RTF file that would be viewed in the Windows Explorer preview pane. This makes this vulnerability even more dangerous.
SEE: Mobile device security policy (TechRepublic Premium)
Attacks in the wild since March 2022
Sekoia reports several cases of attacks in the wild exploiting the Follina vulnerability, the first attacks being probably done by Chinese APT threat actors.
Some documents have been found that target Nepalese companies or individuals.
Another document, entitled “CSAFP’S_GUIDANCE_RE_NATIONAL_AND_LOCAL_ELECTION_2022_NLE.docx” targets several armed forces divisions, impersonating the armed forces of the Philippines (figure A).
Figure A

Sekoia further reports that they could only retrieve one payload still alive at the time of their research, which downloaded an encoded shellcode which once decoded appeared to be a Cobalt Strike beacon. The IP address from which the shellcode was downloaded is known by Sekoia as a PlugX C2 server, PlugX (also known as KorPlug) being a trojan malware used by several Chinese APT threat actors.
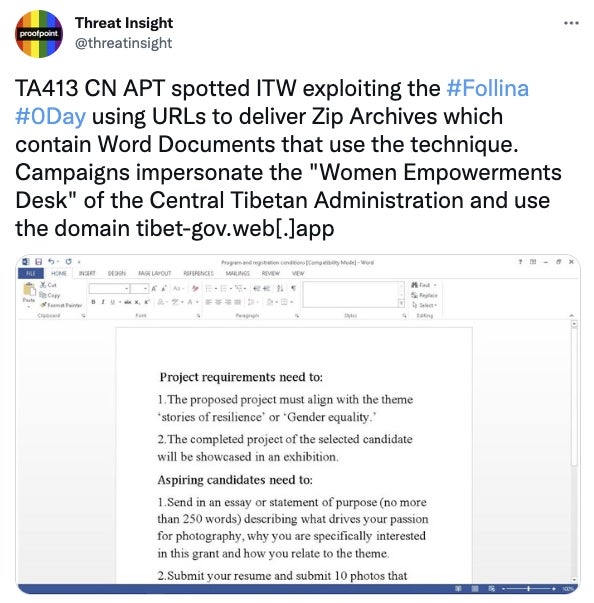
Furthermore, Proofpoint reports on Twitter that Chinese threat actor TA413 has been spotted in the wild exploiting the Follina vulnerability, using Zip archive files which contained malicious Word documents in an attack campaign impersonating the “Woman Empowerments Desk” of the Central Tibetan Administration (figure B).
Figure B
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
How to detect the vulnerability and protect from it
The exploitation of the vulnerability can be detected when msdt.exe legitimate binary is executed with the IT_BrowseForFile argument containing $( string sequence.
Another detection that can be used would be to detect the spawning of sdiagnhost.exe with a conhost.exe child and its subsequent payload processes.
Microsoft has issued a workaround guidance that consists of disabling the MSDT URL protocol directly in the registry.
Disabling the “Troubleshooting wizards” in the registry is also recommended.
Security vendors and antivirus are actively working on improving detection for the Follina vulnerability as well, so it is advised to stay up-to-date on all security products and antivirus solutions.
Furthermore, it is advised not to open or even have a preview at any .DOC/.DOCX file received by an unusual channel: unknown email sender or unknown instant messenger message, for example. It is also advised not to open or preview .RTF documents that would be received.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


